
Authentication is essential for ensuring that only authorized individuals gain access while keeping unauthorized users out. To authenticate a user, we consider three key factors:
- Something a person HAS
- Something a person KNOWS
- Something a person IS
Multi-Factor Authentication (MFA) combines two or more of these factors to verify a user’s identity for login or other transactions. The most common methods of identification are summarized in the following diagram:
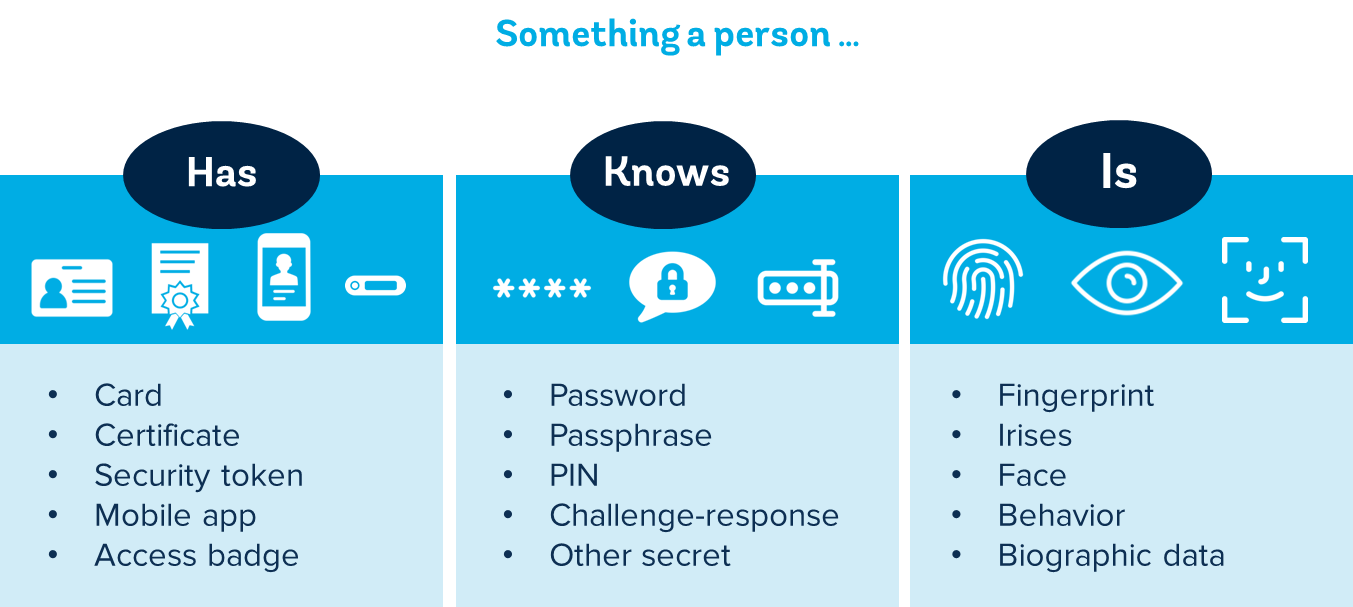 Source: Identification for Development, The World Bank
Source: Identification for Development, The World Bank
Something a Person HAS
Traditionally, physical devices like cards, tokens, or badges with cryptographic certificates have been used to verify this factor. However, replacing lost or outdated physical devices can be slow and costly. With the rise of mobile-first approaches, mobile apps have become the most popular and user-friendly means of authentication.
Did You Know? V-OS uses a proprietary algorithm to bind a mobile app instance to a specific phone, making it impossible to clone the app and run it on another device. In case of phone replacement, V-OS will bind to the new device.
Something a Person KNOWS
Due to social engineering attacks, information known to the user can also be known to hackers. Incorporating time-based authentication and one-time use codes can make it harder for unauthorized users to gain access.
Did You Know? Phishing attempts to steal passwords, which fall under this category. V-Key ID eliminates the need for passwords, making mobile apps resistant to phishing attacks.
Something a Person IS
Given the popularity of mobile apps for authentication, leveraging biometrics is a convenient option for users. Fingerprint and facial recognition biometrics can be used on mobile devices without additional hardware.
Did You Know? While biometrics provided by phones simplify user experience by unlocking passwords or PINs, they still fall under the “Something a Person KNOWS” category. V-Key ID offers true facial biometrics to verify “Something a Person IS” while preserving user privacy.
Not All Authentications Are the Same
With numerous vendors offering authentication services, it’s important to recognize that not all solutions are equal. As cyberattacks become more sophisticated, robust authentication is crucial to secure assets and transactions. V-OS’s virtual secure element serves as the root of trust, ensuring the authentication process is resistant to cyberattacks. Its algorithm makes PKI solutions ideal for protecting high-value transactions and sensitive information. The tight integration to your mobile app makes the user experience seamless.
Can’t I Just Use a Free Authenticator App?
Free authenticator apps are popular and widely used but they’re often built for basic use cases, not high-assurance environments. These apps typically rely on standard mobile OS security, which may not be resistant to tampering, rooting, or malware. Some even allow multiple instances, creating a risk where the same secret keys can exist on both a user’s and an attacker’s device. That’s not true possession, and it’s not true security.
What about paid version from vendor X?
While the paid version of authenticators provides higher level of confidence to the users, they suffer various issues. Some must be used together with the firewall from the same vendor. Some charge by number of transactions. Some even allow downgraded authentication as a fallback through unsecure communication channel such as SMS OTP or email OTP.
Why V-Key?
At the core of V-Key’s product suite is V-OS, the world’s first Virtual Secure Element to achieve FIPS 140-2 Level 3 validation (US NIST), meet FIDO security targets, and attain Common Criteria EAL3+ certification. V-OS creates an isolated virtual environment within mobile applications to securely store cryptographic keys and other critical information. V-OS Cloud is compliant to SOC 2 Type II. V-Key is also accredited by the Infocomm Media Development Authority of Singapore (IMDA).
Using V-Key’s product suite allows organizations to authenticate users easily while meeting various central bank requirements (e.g., TRM from the Monetary Authority of Singapore, RMiT from Bank Negara Malaysia). This approach ensures minimal investment while maximizing security benefits.






































